Safety Instrumented System ( SIS ) Bypass and Impairment
7 min readSafety Instrumented System ( SIS ) bypass by any other name is just as dangerous. Whether referred to as an inhibit, suppression, or forcing, the bypass of a safety system device or automated function nearly always means that this safeguard will no longer be able to provide the full degree of risk reduction and reliability it was specified to perform. Continued safe operation of that facility will usually depend on timely implementation of compensating measures to provide the risk reduction that was lost through the act of bypassing.
The predictable consequences of bypassing a safety instrumented system device or function lead to the following dual requirements for bypass management:
- Features to prevent and alert unauthorized use (and other operator error)
- Highly effective management of change and access security controls.

Safety Instrumented System (SIS) Logics are built with safety interlocks considering multiple safe scenarios for protecting the equipment/plant. The functionality of such logic implemented either in the Basic Process Control System (BPCS) or Safety System (SIS) is very critical for the plant operations.
However, there may be a need to bypass an SIS or BPCS Independent Protection Layer (IPL) function for specific reasons such as startup, testing, or maintenance.
Again bypasses shall be counterchecked and removed for bringing back the equipment to operate in a safe manner. To manage this, there shall be a management system to ensure that a bypass is removed once the condition that required it has been satisfied.
That is, written procedures documenting how and when an SIS bypass may be used, by whom, and for how long, are required, but are not sufficient to meet the requirements of the IEC-61511-1 standard. Regardless of how high quality the procedure is, or how well trained the operator is, the potential for human error will remain. For this reason, features that enable effective access restriction and otherwise protect against operator error using the bypass are required in addition to the management controls. In the correct use of bypasses during continued operation, alternative means of providing risk reduction (compensating measures) are used to manage the process safety risk gap created by the approved bypass activity.
Also Read: What is the difference between fall protection and fall prevention
Events that may trigger the use of a bypass:
Typical hazard and risk analysis (H&RA) practices assume that safety controls, alarms, and interlocks (SCAI) will be in service nearly all the time, so the best situation is to not have bypass capability at all. Indeed, SIS is required to be designed in such a way that the need for using a bypass to continue operation while an SIS device or function is defeated is minimized. The justification for SIS bypasses should be periodically reviewed by facility management to ensure the removal of bypass features that no longer have sufficient reasons to exist. However, sometimes these piping and design features are needed in order to facilitate timely online preventative maintenance, proof testing, and repair of diagnosed failures. As a result of being part of a planned and scheduled activity, this kind of bypass use will usually occur during an inherently safer time (such as during a planned turnaround) or in an operating mode where compensating measures are available.
Unfortunately, not all bypass activities will be planned in advance. Suspected failure of an SIS device may create a demand for an online inspection and repair during continued operation. This potential SIS failure may be detected through the poor performance of associated equipment. In this case, the actual cause of the deviant equipment behavior may not be immediately evident. Such an unplanned operating situation creates human factors that are far less favorable to the successful execution of a complex task such as evaluating the safety of continuing operations. Fear of reprisal from leadership or peers for taking a too conservative approach, incorrect assumptions regarding the reliability of the information being presented on the automation system, and the simple desire to “do a good job” can combine during a crisis event to lead an otherwise experienced operator to bypass a safeguard at precisely the wrong time. Having detailed written bypass procedures that include clear instruction regarding the conditions a bypass may be safely used can address a portion of this risk.
Bypass Rules
Written procedures shall exist for any hardware or software that permits bypass of an SIS function.
For SIS, BPCS IPL safety functions, procedures to be made available to update, edit & Bypass (as and when required), and required System Access restrictions. The approach is applicable to all new installations, retrofits, and upgrade projects.
For BPCS protective function maximum time allowed for an instrument out of service should be minimized and be limited to 14 days.
Necessary Management of Change (MOC) policy must be followed so that safety will be assured by other technical or administrative controls and shall consider the availability/bypass condition of other protection layers for affected scenarios. The terminology may vary depending on the plant.
Bypass Requirements & Restrictions
- By-pass switches must be protected by a key lock or password to prevent unauthorized use.
- The indication must be provided that the SIS is bypassed by the alarm in DCS / Annunciator panel and/or develop the procedure.
- Where a by-pass is required it should be installed such that alarms and manual shutdown facilities are not disabled.
- Proper care to be taken for Bypassed instruments, valves also to be tested as part of SIS validation (when required).
- Operators must be trained on the operation of the by-pass and requirements when it is to be used.
- SIS design must minimize the need to impair the SIS while the unit is running.
- Operation and maintenance procedures must be developed which provide the actions and constraints necessary to prevent or mitigate the hazard while the SIS is impaired.
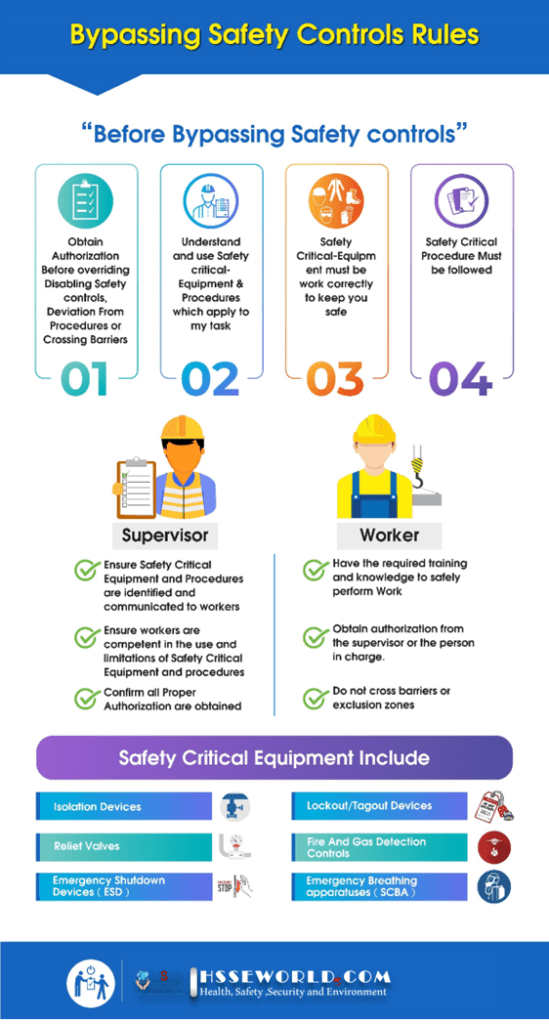
Also Read: Photo of the day: Bypassing Safety Controls Rules
Physical Hardware Restrictions
- Bypass valves installed around SIS “Final elements” must be secured in the “safe” position (typically, this is the “closed” position) with mechanical locks or car seals.
- A management system must include:
- Control and access to lock keys or a half-yearly audit procedure for ensuring the integrity of seals.
- In-service operation of a bypass valve requires a written procedure which includes:
- Approval by the relevant Business Head and the Process Safety Leader.
- Actions that are necessary to prevent an unsafe state
- Must ensure that the time the bypass valve is actually used is minimized
- An inspection of the block valve to ensure that it is returned to the secured “safe” position.
Physical Software Restrictions
As part of the software, it requires access restrictions for operating bypasses around SIS components. However the implementation of “access restriction” is more stringent and requires “physical” restriction:
It is recommended that the bypassing must be “annunciated” visually or audibly.
Safety System Impairment
To protect against inadvertent bypassing of the protective function: software, hardware, and/or written procedures to be used so that the act of bypassing is annunciated and access-restricted – Implementation of the Safety System Impairment Standard is recommended.
If “written procedures” are chosen as the method of preventing inadvertent bypassing, implementation of the practices to meet the intent of this requirement.
Background
- Need the ability to test Safety Instrumented System (SIS) when the plant is in operation.
- Plant owners finalize Impairment requirements so that temporary safety system outages, impairments, and bypasses are always managed properly.
Brief Examples of SIS Impairment
What does it mean to “impair” a safety system?
Here are a few examples….
- If a Safety Function requires a valve in a steam/gas line to close when activated, the scenario may not be prevented if a bypass valve is open around the SIS final element.
- If a Safety Function requires a cooling water valve to open, the upstream block valve is closed, the scenario may not be prevented.
- Similarly, the SIS function may not be functional if software logic bypasses and closure of block valves in sensor lines.
- For instrument root valves: If the valve is clearly visible as an instrument root valve, SSI is not needed and the valve does not need to be locked open or tagged. This is because plant operations will not be using this valve to operate the plant. Since the instrument will have a Safety Instrument identification tag, this should be sufficient to alert maintenance personnel that the root valve will disable an SIS. However, if the root valve is located remotely from the instrument, it may not be obvious to operations that this is a maintenance valve. In this case, the SSI process should apply.
Summary:
The written bypass procedure provides the necessary information to the operator, such as the correct way of using the bypass and expected restrictions for use. Operators must be trained on these procedures and the correct use of SIS bypasses should be included in the content of the periodic competency assessment required for operators performing safety lifecycle activities. However, the systematic conditions that usually surround the unscheduled use of an SIS bypass feature increase the probability that the operator may make an error in judgment regarding whether the use of the bypass is sufficiently safe. It is the effective implementation of access restriction that ensures there is the opportunity for independent confirmation of the appropriateness of the proposed bypass activity and for verification that compensating measures have been put in place prior to the impairment of the normal source of protection. For sustained effectiveness of the bypass management and countermeasure program, functional safety audits should ensure:
- Justification for bypass capability is reviewed on a periodic basis by management
- Keys and passwords are kept secure in order to remain effective
- Devices used for compensating measures are maintained and managed
Also Read: Process Safety and Instrumentation control system
Please visit our Safety Resources SAFETY BAG to have many Safety Resources




